Previously I had written about how can we disable targeted ads on various social media and e-commerce sites. But opting out from targeted ads doesn't mean you would stop seeing ads on the websites or those sites will stop tracking your activities throughout the internet. The majority of the tech-savvy internet users mandatorily have an ad blocker in their browser. But that isn't enough since most internet browsing also happens on mobile devices. In this post, I aim to touch upon how most of the ad blockers work and how we can utilize the same logic for blocking ads and tracking on entire networks and mobile devices without rooting your android phone or installing non PlayStore apps.
Concept behind blocking
To quote uBlock's GitHub Readme, it is not just ad blocking, it is content filtering. To simplify what they are trying to say, the thought process behind any blocking software is filtering out known advertiser and tracker DNS names. EasyList is one of the most used lists of possible advertiser domain names and also URL patterns. EasyList in particular uses a syntax that is consumed by supported ad-blocking browser extensions like AdBlock Plus, AdBlock, uBlock Origin.
Tools
Blocking using Browser Extensions
For most internet users, blocking ads is primarily through browser extensions. Most used and trusted ad blocker extensions are AdBlock Plus, AdBlock and uBlock Origin. Along with ad blocking, these tools also perform functions like stripping the block where the ad was removed instead of showing an empty area, customizing the preset block list, whitelisting sites that should be allowed to show ads, etc. The main problem with using these browser extensions is that they can block the ads and tracking only on the laptop/desktop browsers. We will discuss how to extend the ad blocking functionality to mobile devices in the next section.
Blocking ads throughout the network
Even though I have ad blockers installed on my computer, most of my family's internet browsing happens through their mobile phones. Since the phones were from Xiaomi, they would see ads not just in the websites they open, also throughout the operating system (I had managed to turn a few of them off, but there were some in-built apps where ads were not optional). During my search for a solution to block ads on their phones, I found few apps like AdGuard, they were official published in PlayStore and we had to download the APK manually and install them. The other problem with AdGuard was few of the features needed the phone to be rooted, which did not feel like a suitable solution for me.
Then I came across Pi-Hole, which is a DNS level blocking and monitoring software that can run on docker or a Raspberry Pi. When installed on Raspberry Pi, we can use that as a DNS server for our local home/office network to filter domain requests before they are forwarded to an actual DNS server like Google or Cloudflare. After reading about this tool further, I bought a Raspberry Pi Zero and installed a pi-hole on it. Now, all of the DNS requests in my home network first go through the Pi Zero, get validated in Pi-hole, and then goes to my DNS server (CloudFlare 1.1.1.1). But there is a catch, just installing Pi-hole and setting it up as DNS Server won't cut it, you will have to tell the software which DNS servers to block and which not to. Pi-hole's web interface allows us to configure it with millions of domain blacklists available on the internet. Some of them provide specific blocking like ads, malware, tracking, etc. Along with that, you can add any website name to blacklist or whitelist through their web portal.
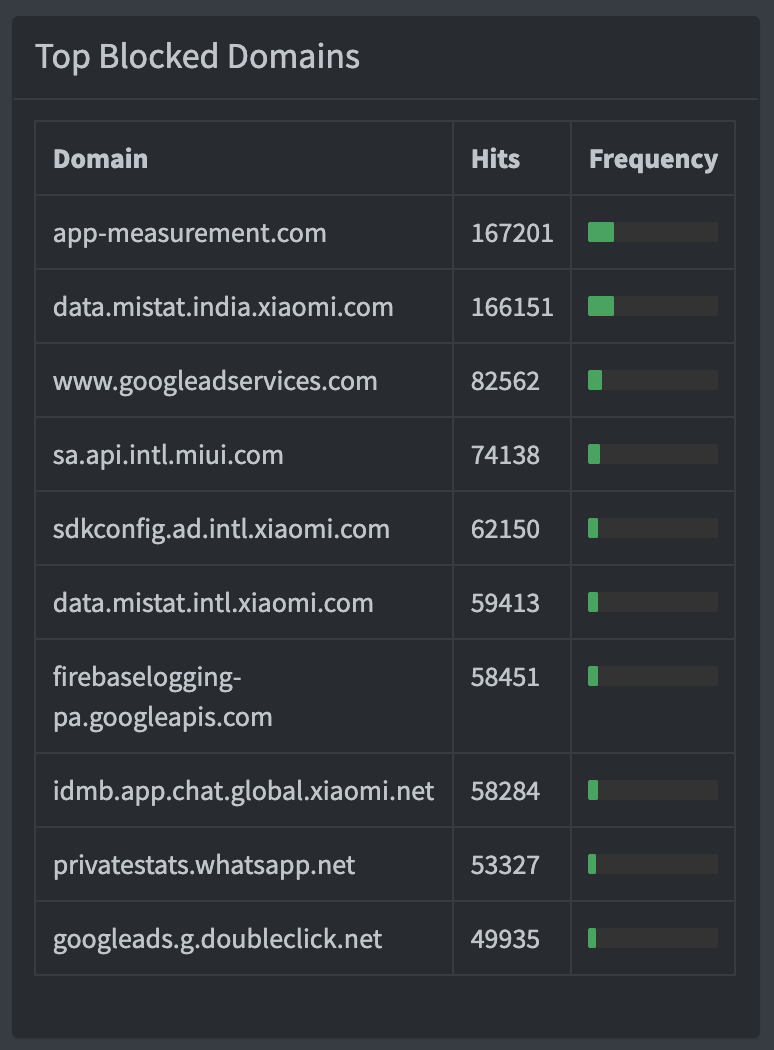
After digging through a lot of websites for blacklists, I ended up with roughly 1.5M blocked sites on my network. The lists were so extreme that I had to then find and whitelist sites like Google Fonts, Sentry. One thing I found out after running this for a year is that no matter how much you opt-out of activity and usage tracking, companies like Google and Xiaomi ping data now and then from the devices to app-measurement.com (Android Activity Tracking) and data.mistat.india.xiaomi.com. Here are the all-time top blocked sites in my network.
If you are now thinking of setting up a Pi-hole in your network, I would suggest you look at the setup guide on linustechtips.com. The other obvious advantage with Pi-hole is that you can get known malware, spyware, crypto mining, and phishing site lists and blacklist them. Here is the list of blacklists that are configured on my Pi-hole.
- https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
- https://www.github.developerdan.com/hosts/lists/tracking-aggressive-extended.txt
- https://www.github.developerdan.com/hosts/lists/ads-and-tracking-extended.txt
- https://raw.githubusercontent.com/unknownFalleN/xiaomi-dns-blocklist/master/xiaomi_dns_block.lst
- https://raw.githubusercontent.com/r-a-y/mobile-hosts/master/AdguardMobileSpyware.txt
- https://raw.githubusercontent.com/crazy-max/WindowsSpyBlocker/master/data/hosts/spy.txt
- https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-malware.txt
- https://raw.githubusercontent.com/anudeepND/blacklist/master/adservers.txt
- https://raw.githubusercontent.com/anudeepND/blacklist/master/CoinMiner.txt
- https://gitlab.com/Kurobeats/phishing_hosts/raw/master/hosts
- https://dbl.oisd.nl/
Blocking ads on Android without rooting
After seeing that roughly 40% of the DNS requests were getting blocked by Pi-hole due to ads and tracking, I kind of become very hesitant to use mobile internet and always wanted to be in the Pi-hole configured network. But that wasn't possible practically. So, I searched for a Pi-hole tool for phones which would also work without needing to root the phone. That's when I found personalDNSfilter app. This app operates exactly like how Pi-hole does, it takes a list of blacklists and using the VPN feature of the phone, filters the DNS requests within the app. It comes with a preset of blacklists that can be enabled according to your convenience. Just to have consistency, I went ahead and copied all the blacklists from my Pi-hole to the personalDNSfilter app. Since DNS requests for Ads and Tracking are not leaving your phone, you would also save on your mobile data.
Honorable Mentions
Most of the tools I have mentioned are free and open-source, if you find them useful consider donating for their development and maintenance.